TNS Experts
This post was submitted by a TNS experts. Check out our Contributor page for details about how you can share your ideas on digital marketing, SEO, social media, growth hacking and content marketing with our audience.
Data privacy is a huge public concern of the digital age. Know the best practices outlined here that can help your organization create a baseline privacy framework for becoming a responsible and ethical steward of personal data.
Data is one of the most sensitive assets in every organization. The rate at which information increases is almost exponential, attracting several agencies to set up laws and regulations to govern how such data should be collected, stored, used, and even transferred from one party to another. To help you stay compliant with the various data laws and protect sensitive data from digital invaders, we've rounded up some data privacy and security basics below.
Most organizations and businesses use the terms' data privacy' and 'data security interchangeably, which shouldn't be the case. Data privacy governs how data is collected, stored, shared, and used, while data security is all about protecting data from external attackers, malicious insiders, etc.
In other words, data privacy deals with compliance with data protection laws and regulations. On the contrary, data security defines an organization's measures to prevent unauthorized third parties from accessing data.
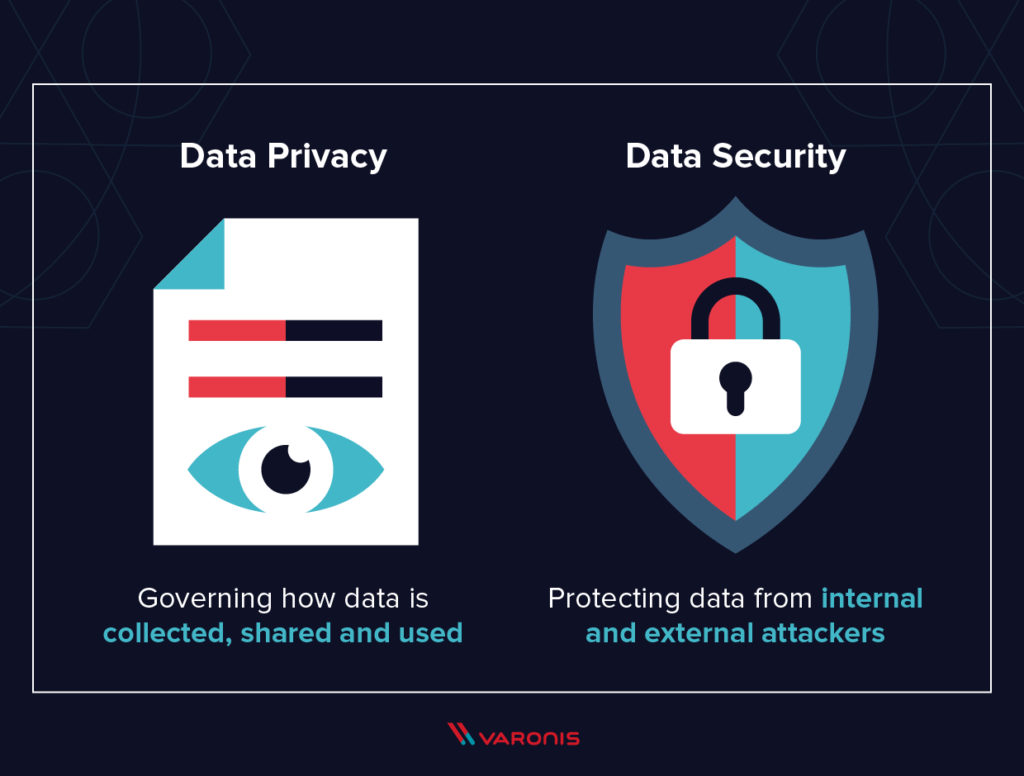
To ensure compliance with the various data protection laws, you need to clearly distinguish between the two. Safeguarding sensitive data narrows down to having the proper data privacy and protection measures in place, such as:
The other measures that cut across data privacy and data security include building trust and transparency about the customer and employee data that your company has collected. This takes us to our next data privacy essential.
Trust in business is hard to come by. By understanding the needs of the employees and the customers and choosing to be deliberate in your actions, you can nurture an environment of mutual understanding and cohesiveness. Being honest, consistent, and accountable about the employees' and customers' data is key to building long-term relationships where both the data owner and data custodian are reading from the same page.
The most successful companies have built trust with their customers and employees, allowing them to use data when need be, for the right reasons, and to further causes that are beneficial to all parties. That said, effective and consistent communication is key to building trust. For instance, every company should educate the employees or customers about their rights to data ownership, including the steps they should take when they feel their data rights have been violated.
Teaching transparency and demonstrating it are two different things. C-suite leaders, e.g., the CIOs down to the line managers and supervisors, should be proactive in building trust through effective communication and engagement. The idea is to let the data owners know that their sensitive information is safe. Letting them know that they have total control of their data will build on their confidence and further boost their cooperation and goodwill.
The truth is, that data privacy is more sensitive, broad, and complex than data security. The latter lies more with the measures that an organization should put in place to protect against data loss or access by internal or external invaders. Over the years, the data security landscape has evolved to comprise new technologies such as zero-trust security infrastructure deployed on-premises or in the cloud. In other words, the company's I.T. team can work on data security without necessarily involving the customers or other employees.
On the other hand, data privacy is all about communicating the whys and how sensitive data is collected, stored, or used. There's also no obvious definition of what data privacy really is. Several laws and regulations governing this subject are somewhat diverse, each stating a set of best practices and the rights of consumers and businesses.
Implementing data privacy policies always begins with understanding how any piece of data or information is gathered or used. But even with online privacy laws, data privacy threats such as identity theft, spam calls, or online blackmail are hard to get rid of. Curbing such challenges narrows down to taking a proactive approach to strengthen the walls of your online privacy.
Whether you are the CEO, CIO, or an ordinary employee, data privacy starts by keeping your online data safe and staying vigilant about data privacy trends. Here are a few tips you can implement on your own or across your department or company:
The above three steps are just but a few ways to strengthen data privacy at a personal, department, or organizational level. Creating a future-proof data privacy strategy requires a proper understanding of I.T. technicalities and the legal aspects of data privacy and security.
Most industries such as healthcare and financial institutions have specific data privacy laws that govern how the data generated within these industries should be handled. To further understand the various data privacy laws, let's look at the popular statutes and regulations governing data privacy.
Popular Data Privacy Regulations
Below are some of the most popular data privacy laws and Acts governing how companies, agencies, and businesses should handle end-user data.
Failing to comply with any of the above data privacy laws can lead to serious legal claims and litigation issues, resulting in hefty fines and legal fees. According to a 2020 cost of data breach report, the average total cost of a data breach is around 3.86 million U.S. dollars. The report further estimates that an organization can save approximately 1 million U.S. dollars by containing a breach in less than 200 days.
To further understand the consequences of data breach and non-compliance, below are three examples of the top breaches – from how they happened, the fines, penalties, and everything in between:
In January 2020, digital invaders gained access to 5.2 million sensitive records of Marriot guests. The exposed data included names, phone numbers, emails, passport numbers, birthdays, gender, and even personal preferences. The attackers used a third-party app to compromise the login credentials of two Marriot employees and gained access to the network without being noticed for two months. U.K. regulators found that Marriot was negligent in securing the customers' data in their system and resulting in a fine of approximately $124 million.
In 2018, Uber was hit with a $148 million fine for violating the data breach notification laws after paying hackers $100,000 to keep a data breach secret. During a data breach, which occurred in 2016, cybercriminals gained access to 57 million user accounts and more than 600 000 drivers. The rideshare company tried to cover the bad P.R. by paying the attackers, but it later came to the limelight.
The 2017 Equifax data breach is one of the infamous cybersecurity incidents of all time. The company failed to update the Apache Struts framework (a developer platform used to create and maintain web applications), which has a critical vulnerability. Equifax didn't fix the bug when the update was first available, resulting in a data breach that resulted in a loss of personal and financial information of around 150 million people. After agreeing to pay penalties and fines for negligence and failing to disclose the incident for weeks, the total cost amounted to $1.4 billion, not including legal fees.
Cybersecurity is no longer the fancy term C-suite executives used to speculate while reading some technology trends from the newspapers. Nowadays, small and large businesses alike are at risk of cyberattacks, and the need to stay updated on the issue is now a priority.
Investing in the latest threat protection systems, such as Zero Trust and Blockchain technology, have a significant impact on your overall preparedness to handle cyber threats. However, developing a culture of security where everyone within the organization is on board with the company's cybersecurity policies is by far more important.
The benefits of having all the employees focused on shared goals means that everyone will be on the lookout for data privacy and security loopholes as well as data compliance issues. That also means all your employees will support the cybersecurity policies at will without necessarily imposing strict consequences for employees who fail to comply. In other words, to maintain a robust cybersecurity strategy, you need to understand your company's weak points and work on solving them since you are only as strong as your weakest links.
Staying compliant with all the data privacy laws will probably require help and guidance from an expert legal professional. On the other hand, ensuring the best data security comes down to understanding your company's cybersecurity framework and implementing proper mitigation measures to reduce exposure to data vulnerabilities.
You’ll also receive some of our best posts today
This post was submitted by a TNS experts. Check out our Contributor page for details about how you can share your ideas on digital marketing, SEO, social media, growth hacking and content marketing with our audience.
Artificial Intelligence has been posing opportunities to the eCommerce...

User reviews are a game-changer for e-commerce. Consumers rely heavily o...
Don’t miss the new articles!