Anas Hassan
Anas Hassan is a Content Marketer at a leading cybersecurity firm PureVPN. He has vast experience in the field of digital transformation industry. When Anas isn’t blogging, he watches the football games.
Considering how technology is evolving daily, it is unsurprising that cybercriminals have more tricks up their sleeves. Protecting your digital privacy against these attackers can be difficult but never impossible! Check out this comprehensive guide to learn our best tips to guard your online presence effectively.
When we say that a cybercriminal does not care whether you are a dedicated employee or just a person trying to enjoy another Netflix binge, we mean it! That is because any stolen information is worth gold for a hacker.
Selling confidential company data, worth more than your Netflix password, is inevitable. It would help if you put more effort into protecting your online privacy to avoid landing in such a situation.
Implementing certain security practices and following general rules can help you enjoy a more secure browsing experience! Get things under your control while securing your digital privacy with our five best security steps.
From good password practices to general security awareness, you will need it all to protect your digital assets and surf around more securely. Let's get right into it:
A regular person with an average life would feel like they have nothing to worry about. Why would a hacker hack them? But don't be mistaken! According to recent research, there is a victim of cybercrime every 37 seconds!
We risk our digital privacy every day by just being online. Here are the most common threats to your online privacy:
Data breaches rank high on the spectrum of digital threats. During a security breach, attackers exploit your network vulnerabilities and compromise your system. A hacker then has free access to your data and can use it as they wish.
According to The New York Times, Yahoo suffered from one of the worst data breaches ever, where around 500 million user accounts were compromised.
Hackers, online platforms, data brokers, and even governments can monitor and collect your sensitive information, preferences, and opinions from your Internet activity for selling purposes. Here is how Americans feel about general control over their data according to research led by the PEW Research Center:
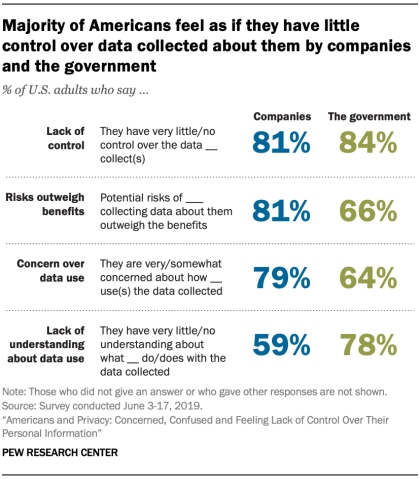
Preferences and sensitive information are often shared with various social media platforms and advertising markets to show ads tailored to your needs. So, if you ever wonder why that bougie handbag suddenly appeared on your feed after your little chat with a friend, now you know why.
However, if you are undergoing an attack, it will be more specific. Cyber attacks come in different shapes and forms with their identifiers. It can be tricky to pinpoint precisely which type of breach you are going through. Here are some common cyber attacks plus ways to identify and deal with them if need be:
Phishing attacks can trap normal users by linking malicious sites in spam emails. Such attacks trick you into leaking credentials or downloading malware from authentic-looking websites.
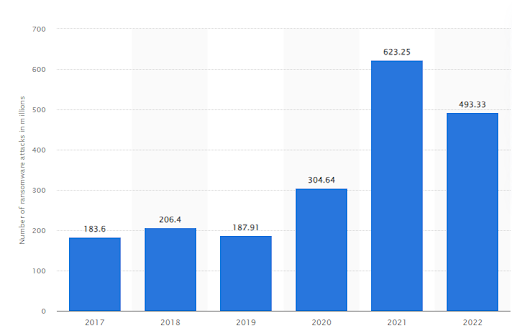
These are the most basic forms of cyber attacks and can infect systems and lockout data, so you must pay your way out. According to security statistics, there were over 623.3 million ransomware attacks in 2021 alone.
If you have a website, you should fear a DDoS attack. Such an attack can overwhelm your servers and shut down operations. According to research, 70% of organizations suffer from 20 to 50 monthly attacks!
A MitM attack can intercept communication without a user's knowledge. It allows an attacker to pay, eavesdrop, collect and modify information.
Hackers attempt to access your accounts by stealing your credentials or passwords using various password attacks. Brute-force attacks, dictionary attacks, and credential stuffing are common types.
According to a study by the European Union Agency for Cybersecurity, here are the most common types of attacks for small-sized enterprises:
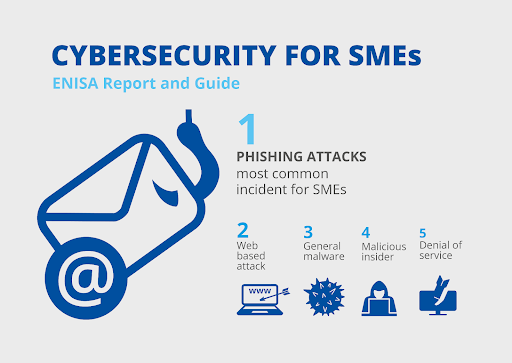
While various types of security differ in specifics, most follow similar principles. The general phases are commonly called the cyber kill chain or attack lifecycle. Here is a generalized overview of the stages of a cyber attack:
A hacker first collects information about their target that could help them fabricate the breach. They identify potential weaknesses, vulnerabilities, and other general information.
The attacker uses the collected information to access the victim's network or system. They can exploit vulnerabilities or gain access via phishing attacks, malware downloads, etc.
The attacker seeks to gain further information about the victim's network and to seek out other vulnerabilities to exploit. They move deeper and deeper into the network, hoping to gain access to higher privileges or other sensitive areas.
The attacker will then extract sensitive information and data and plant means to prolong their access. Backdoors, malicious software, trojans, etc., can be utilized to manage this.
The attacker removes all traceable links to protect themselves from being tracked down. It means that they erase any sign of their presence. Modifying timestamps and deleting log files are common ways.
After all of this, an attacker would generally sell the information for a sum on illegal trading platforms, like the dark web. They can also contact the concerned authorities and ask them to pay a ransom amount to protect their stolen information.
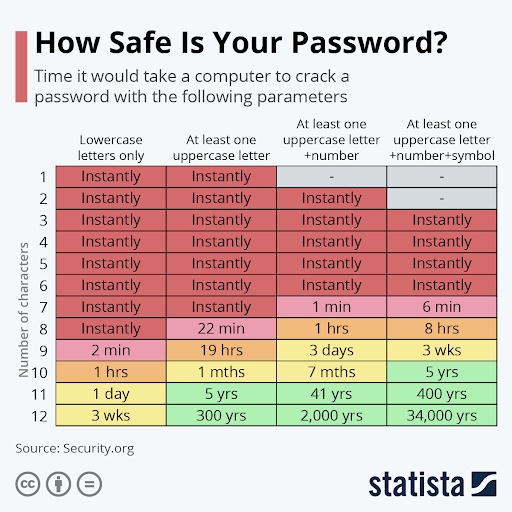
Using strong passwords is extremely important and cannot be stressed enough. A compromised password also easily compromises your digital privacy. Therefore, it is the first step to protecting your online presence.
Avoid common phrases like qwerty and go for something more complex, like passphrases. Something like nO6#$&lI4%%F2m8rA2!t is a good example, as it is long (more than 15 characters), uses both cases, is random, and uses special characters and numbers.
You can even use password managers to create and store your security keys in an encrypted form for maximum security. This tool makes your life much easier as you do not have to juggle your passwords further.
A virtual private network or VPN is a service that helps encrypt your network connection so that you can communicate more securely. The encrypted tunnel is crucial as it prevents your information from getting intercepted and adds an extra security layer to your network.
You can even use public WiFi at your favorite cafe with a reliable VPN. And the best part is that a VPN has much more to offer. Using this tool, if VPN is not connecting, you can even hide your IP address for complete anonymity, bypass content restrictions, get early access, enjoy regional discounts, and even get around IP bans!
If you use social platforms often, this security measure is for you! Your devices, apps, and social media accounts offer options for managing your privacy settings. Ensure you regularly review them to limit how your data is collected or shared with third parties.
You can control who views, comments, shares, or likes your posts. This is crucial because it can limit your exposure and protect your digital privacy. It will help you keep your data and accounts away from cybercriminals and prevent them from snooping around your social media.
Security experts also recommend you use two-factor authentication (2FA) or multi-factor authentication (MFA) to protect your digital privacy.
This technique implies that you need a second verification form (besides your password), primarily a code sent to your email or phone to log into your accounts. Two-factor authentication (2FA) or multi-factor authentication (MFA) helps to reduce the chances of a forced breach or password attacks.
Lastly, it is crucial to keep your systems and applications up-to-date. For this reason, manufacturers release software updates and patches regularly. These help remove any vulnerabilities that an attacker can later exploit.
If not addressed, these weaknesses can compromise your system and data. You can also use various tools to keep your system up-to-date and run regular scans to catch any unusual activity. Automatic update settings and reliable antivirus services are an excellent place to start!
Just like you must adopt certain eating habits to protect your health, you must also assume some secure browsing habits to protect your digital privacy! Here are some of our best security tips to protect your system and data against cyber attackers:
All in all, you must remain vigilant and protect your digital privacy using the abovementioned ways. Experienced security experts recommend all these security tips! They are also go-to measures to help protect your system against a breach.
While it is impossible to protect your system against a breach completely, you can always soften up the blow of a cyberattack whenever you encounter one. Having these measures in place helps you mitigate the issue and sometimes stop an attack in its early stages.
System analysis also assists with monitoring system activity and is crucial for reducing damages in case of a security breach.
You’ll also receive some of our best posts today
Anas Hassan is a Content Marketer at a leading cybersecurity firm PureVPN. He has vast experience in the field of digital transformation industry. When Anas isn’t blogging, he watches the football games.
Emotional Intelligence (EQ) or EQ remains a relatively unknown...
The world is ever-evolving. From the continuous stream of...
With the ever-growing popularity of mobile and the internet,...

User reviews are a game-changer for e-commerce. Consumers rely heavily o...
Don’t miss the new articles!